By: Geeq on Feb 7, 2020
The Security of Geeq’s Public Blockchains
If blockchain is truly permission-less, or public, then anyone can participate. There are no laws, no rules, no stopping anyone from participating or attempting to do so.
The genius behind Geeq’s public blockchain platform is: EVERYONE gets the same, clear opportunity to behave well and reap the rewards.
Geeq believes in freedom of choice – a clear upside for all. The downside, of course, is there are others who may try to do you wrong. It’s rational to be wary of what others might do. In fact, uncertainty about the security of blockchain was one of the major barriers to adoption in 2019.
Introducing Edge Security
Geeq solves this with its many security layers, the last of which is Edge Security. Edge Security empowers you with clearly defined tools that allow you to distinguish whether any node is worthy of your business or not. You simply need to learn the two habits needed to use our blockchains with confidence.
All users who are honest – and always practice these two simple habits – have proof their tokens are safe. In short, all honest users’ transactions will be validated correctly and their tokens cannot be stolen.
What are these two habits?
(1) Keep your private keys safe.
Yes, this rule is true for every blockchain or cryptocurrency.
If you share or lose your private key, then your tokens can be stolen on any platform, including Geeq’s . Some users will, unfortunately, attempt to trick you for your information that is not meant for them or may even try and brute force their way into your wallet. Practice safety and good security measures like never having text files with your key information anywhere open to the internet.
Tokens also become inaccessible if you lose your private key. Because the Geeq platform is decentralized, there is no way we can recover your private keys for you. The good news, of course, is Geeq has no access to your account. So – this is really important – keep your private key information safe. (Here’s a handy guide at the time of this publication.)
(2) Use Geeq’s Edge Security. Only use honest nodes.
Geeq’s proprietary technology is the only one that allows any customer to find provably honest nodes. Which makes it easy for users.
Demand that a node provides you proof that it’s honest before you rely on it. That’s it. If it does, you’re safe. If it doesn’t, putting it bluntly, don’t have anything to do with it – you can’t trust it. Find another node.
The Edge Security Habit
A user of a permission-less or public blockchain contacts the blockchain by querying a node.
Geeq blockchains are completely permission-less at both the validation and the application layers by default. That is extremely convenient because any node can enter or exit at any time. However, it means nodes are able to be anonymous, which is a way that blockchains without Proof of Honesty open themselves to security issues. These blockchains either close their ecosystems and become private, which defeats the purpose of blockchain as a decentralized technology, or require their users to assume there are a sufficient number of honest nodes in the network to ensure the security of the overall blockchain.
Information is an Advantage
Geeq, however, provides a user interface that allows the user to check the node you’ve reached first.
It’s as easy as looking both ways
before crossing the street.
To illustrate, this is what happens when a user contacts a node for a Geeq blockchain.
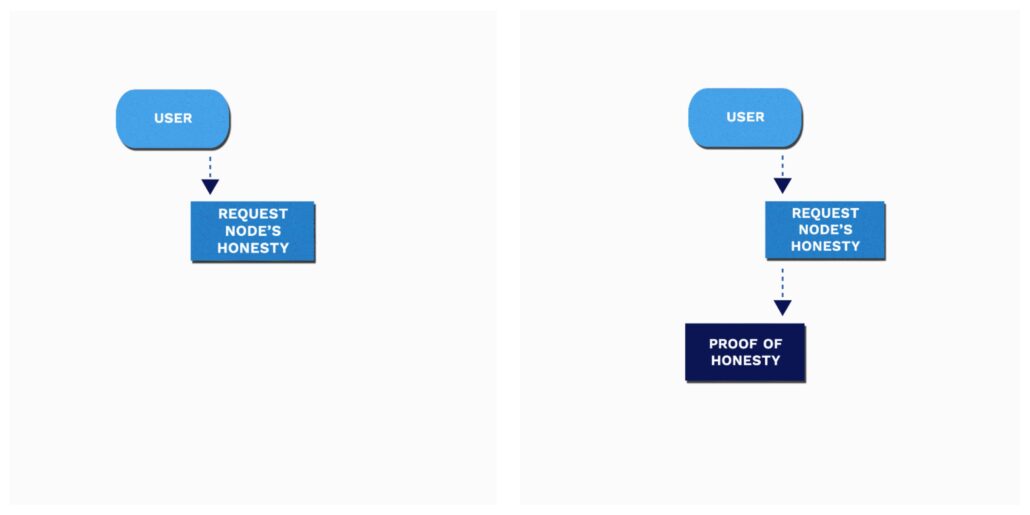
Protect Yourself
What happens if the person running a node on the blockchain is either dishonest or otherwise is unable to provide proof of its honesty? (The latter case covers an honest node that is trying to participate, but is somehow prevented from joining the network.)
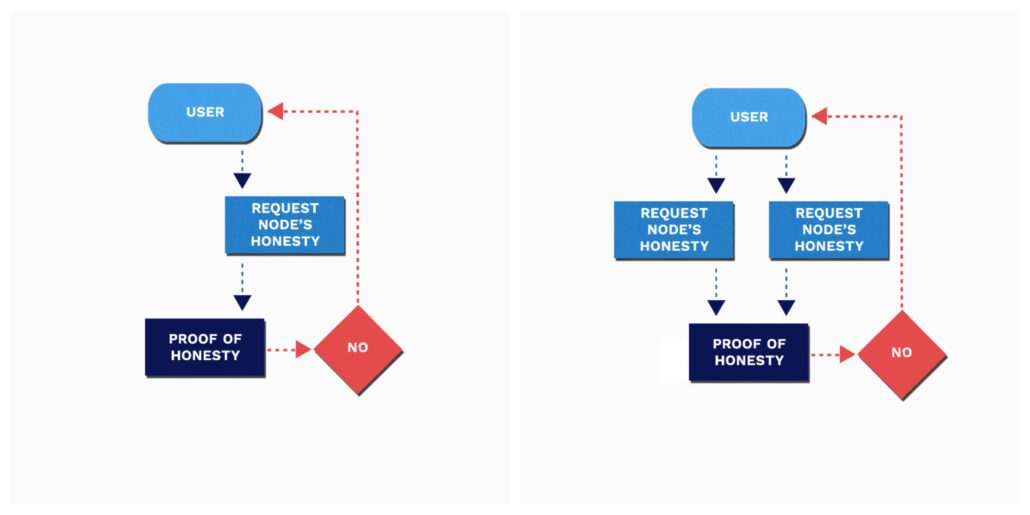
From a user’s point of view, it doesn’t matter why a node won’t offer you proof. Don’t use it. Ask for another.
All Clear? Go!
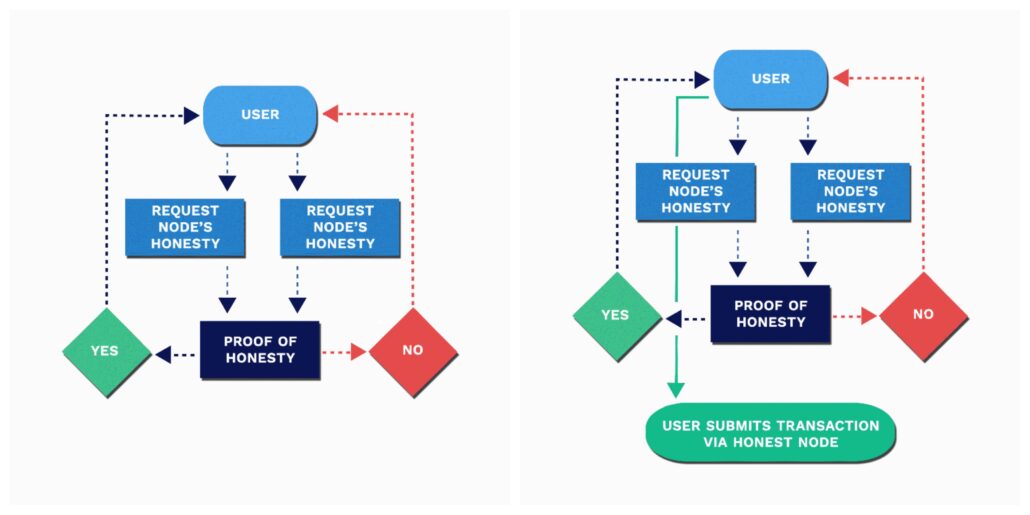
Conclusion
Demand a node’s Proof of Honesty and act upon the response accordingly, On Geeq, using blockchain with confidence is as simple as making sure to look before crossing the street.
Edge Security is the feedback that non-technical blockchain users needed, to feel secure about truly decentralized blockchain.
Photo by Kristin Charleton on Unsplash






To learn more about Geeq, follow us and join the conversation.
@GeeqOfficial