By: John P. Conley on Sep 7, 2019
Geeq is based on a new blockchain consensus protocol called Proof of Honesty(PoH). PoH empowers users who hold tokens on the platform to determine for themselves whether the network of validating nodes is behaving honestly. This allows Geeq to provide 99% Byzantine Fault Tolerance (BFT) while delivering rapid transaction finality at extremely low transactions cost. An additional protocol based on economic mechanism design gives Geeq Strategically Provable Security (SPS). Geeq’s multi-chain architecture creates an ecosystem of interoperable instances that can safely share $GEEQs (the platform’s token) and native application tokens while supporting almost any type of internal business logic. This makes Geeq suitable for a wide variety of use cases, allows for upgrades and bug fixes without breaking protocol or instituting hard forks, and offers a flexible and more secure platform for startups and DApp developers who wish to take full advantage of blockchain’s potential. The $GEEQ itself is a stabilized-token supported by an innovative algorithmic monetary policy designed to reduce price volatility and make $GEEQ a less risky store of value and a more attractive medium of exchange.1
Table of Contents
1. Introduction
Blockchain has the potential to provide secure, uncensorable, and decentralized ways for society to interact, transact, and cooperate. As a source of provable and immutable truth, blockchain makes it possible for widely distributed agents, including machines, who neither know nor trust each other to create and share value. Blockchain can even serve as a counterbalance to the growing power of governments, corporations, and other centralized authorities.
Unfortunately, blockchain technology has a way to go before it can realize this potential. Existing platforms are not very secure, are expensive and difficult to use, and would be hard to deploy at any meaningful scale. The extreme volatility seen in cryptocurrency markets has undermined public confidence in their value as a form of payment and even more so as safe stores of value. Thousands of public infrastructure and Distributed Application (DApp) projects are underway or have already been launched. Nevertheless, the overwhelming majority of transactions volume are simple payments on the Ethereum and Bitcoin networks or take place on private, permissioned platforms such as Ripple and IBM’s Fabric.
Geeq’s objective is to take public blockchain to the next level. We propose a new blockchain consensus protocol called Proof of Honesty (PoH) that looks to users as the ultimate source of authority and truth instead of allowing that power to reside with the nodes on the validation network. Proof of Honesty is 99% Byzantine Fault Tolerant2 (BFT) and gives Geeq Strategically Provable Security (SPS), a guarantee based in noncooperative game theory. In contrast, blockchains using Proof of Work (PoW), Proof of Authority (PoA), Proof of Stake (PoS) can only offer between 33% or 50% BFT. This is simply not good enough if blockchains are to be trusted with critical infrastructure, personal and financial data, stock exchanges, or public records. It is even less acceptable if we view blockchain as a foundation for protecting freedom and privacy.
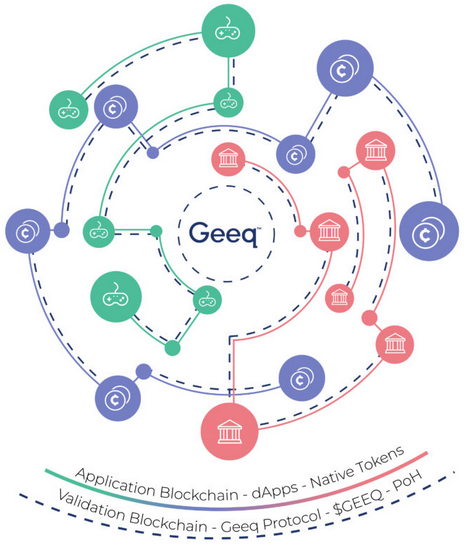
Geeq’s interoperable, multi-chain architecture allows geeqchains to be customized and optimized for a wide variety of use cases. Geeqchains include a flexible application layer that can be designed to follow almost any business logic and have its own native tokens and data types. Native tokens and data can be shared with affiliated geeqchain instances or kept on the instance where they originated. Geeq’s validation layer is entirely separate from the application layer, and each geeqchain instance has its own independent validation network.
2. Why Blockchain?
When there is a central party that can and should be trusted with data, there is no real need for blockchain. Employers keep personnel records in private databases, and manufacturers keep records of inventory, sales, parts, accounts payable, etc. in the same way. This is just as it should be. Similarly, if several parties trust each other, a consortium of banks or hospitals, for example, then synchronized data systems do an excellent job.3
There are five key criteria that make it likely that blockchain as opposed to more conventional distributed data systems or a cloud-based Software as a Service (SaaS) solution is a better approach to addressing a problem:
- The problem requires secure transfer of value, possibly in very small increments; for example, micropayments for content or web services and machine to machine markets, and person to person payments such as small charitable contributions or sharing the cost of a meal among a group of friends.
- The problem involves agents who do not know or do not trust each other; for example, peer to peer markets for goods and services, escrows, and providing proof that all parties are what they say and behaved honestly.
- The problem involves many different actors from different organizations whose interests do not align; for example, logistics or chain of custody applications that transfer responsibilities from party to party.
- The problem requires objective provability of facts or data; for example, audit trails and telemetry4 collected from connected industrial, medical, and infrastructure devices.
- The problem involves agents who might wish to censor, alter, or hide data; for example, securities, land title, and financial transactions where theft and fraud are real possibilities.
For blockchain to offer a viable solution to these problems it must be secure, inexpensive and scalable. For Blockchain as a Service (BaaS) to become a realistic alternative to private databases, it needs to be flexible, upgradable, environmentally sustainable, and protect users from unreasonable volatility in token value.
3. What is Geeq?
Geeq provides an answer to all of these problems. Let’s begin by describing what Geeq is. An instance of a geeqchain is any blockchain that uses Geeq’s validation protocols and architecture (described below). The set of all instances collectively form an ecosystem of separate but interoperable blockchains that make up the Geeq Platform. Each geeqchain extends from its own genesis block created by Geeq which guarantees the integrity of security of the instance.
3.1 The Geeq Genesis Block
All instances of geeqchain begin with a genesis block (block number 0). Blocks of validated transactions are created by nodes in the network and appended sequentially. Genesis blocks are created by Geeq at the request of developers who wish to build applications and include all the code that will run the validation and application layers. This tight control over the form of genesis blocks has several motivations.
- It prevents duplication of chain and token names.
- It ensures the chain adheres to Geeq’s protocols for transaction verification which in turn makes it possible for different instances to trust in the integrity of one another’s ledgers and to accept token transfers from other geeqchains.
- Most importantly, it fixes the rules under which the chain will operate. Including copies of validation and DApp code that nodes are expected to use in the genesis block allows users to do their own audits to verify that the rules are being followed and nodes are behaving honestly.
A founding principle of Geeq is that Code is Law. If a protocol or the ledger of a chain can be altered by foundations, governance systems, collective action by nodes, etc. then the blockchain is neither immutable nor trustless. Instead, users must trust in the wisdom and good faith of those who are actually in control.5
It might seem that this approach gives Geeq a great deal of power. However, once a genesis block is created, neither Geeq nor anyone else can alter it or the operation of the geeqchain instance that uses it as a foundation. There is simply no mechanism to allow such manipulations to happen. Once launched, each geeqchain has a life of its own.
3.2 Geeq’s Upgrade Path
Bugs, hacks, upgrades, new functionalities, quantum computing, etc. all make it desirable to be able to let blockchains and DApps evolve and change over time. When hard forks6 are imposed on unwilling or unwitting users by foundations, developers, coalitions of nodes, or even through complicated governance systems, faith is broken with users and confidence in the platform is undermined.
Geeq’s multi-chain architecture provides an elegant solution to this problem without breaking our core principle that code is law. If an instance of a geeqchain is found to have bugs, has become obsolete, is not taking advantage of new technologies, or is failing to meet current user demands, a new instance can be created with the intention that it replace the existing one. The new chain would have a new genesis block with a new set of validators, validation and application code, but no tokens. Users and validators on the old chain are allowed to choose to move to the new chain where the rules are different, or stay where they are. If they choose to move their tokens, their actions are voluntary and within protocol. If they choose to stay, they can continue to live under the old rules. If enough users and nodes support the continued existence of the original chain, they can trade tokens under the original rules indefinitely.
It will not be long before 256 bit (or greater) encryption can be broken by quantum computers. This will undermine the security models of all existing blockchains and almost everything else in the cloud. Fortunately, with quantum computational approaches to breaking encryption will come new quantum-proof approaches for encrypting data. Geeq’s multi-chain architecture allows the creation of new quantum-ready instances of existing chains and applications for users to migrate to as quantum technology matures.
3.3 Geeq’s Architecture
Blockchains are built on networks of nodes that process, validate, and store transactions. Geeq shares this foundation, but builds a uniquely secure and flexible ecosystem on top.
Geeqchains actually consist of two entirely separate blockchains and ledgers that are maintained in parallel by the same network of validating nodes. This unique two layered approach is what allows Geeq to be flexible and adaptable without sacrificing security.
Geeq’s validation layer is simple and robust. It contains only $GEEQ accounts and manages basic token transactions between users as well as fee payments to nodes for their validation and virtual machine services.
Geeq’s application layer, on other hand, is customizable and can support business logic, smart contracts, DApps, native tokens, and specialized data items to suit almost any use case. For example, the application layer of an instance of geeqchain might be provisioned to run Solidity and allow smart contracts originally written to run on Ethereum to be moved directly to Geeq. Functionality would be the same and data formats and the blockchain that is created on the application layer would look almost exactly like they do on Ethereum. The difference would be that payments between users and to nodes for transactions fees would be written on the validation layer blockchain.7 It would also be possible to build a simple (non-Turing complete) scripting language on the application layer, or even just code designed to run one specific application, if this was all a developer needed.
Geeq’s two layered approach minimizes attack surfaces since the validation layer does not have smart contracts or other complicated features. At the same time, the application layer allows developers to create exactly what they need, without carrying elements for which they have no use on a ledger that is independent of the underlying validation protocol and blockchain.
Geeq also takes a novel approach to establishing and maintaining the network nodes that validate each instance of geeqchain. Anyone who wishes can download Geeq’s node client software and then anonymously join one of the validation networks by submitting a “join Active Node List (ANL)” transaction to an existing node. The join transaction includes an IP address where the node can be contacted and authorization to transfer a certain number of $GEEQs from the new node’s account into an escrow account as a Good Behavior Bond (GBB). The ANL is maintained as part of the ledger that keeps track of users’ account balances. As a result, users are able to learn where to contact all nodes in any given validation network by requesting the ANL from any node.
Bitcoin, Ethereum, and most other blockchains, use peer-to-peer gossip networks to communicate user transactions, distribute newly mined blocks, and transmit other message traffic between nodes. In the case of Bitcoin, for example, users find the IP address of a node and send it a transaction request. This request is then broadcast to a group of peer nodes known to the receiving node, and from there, it spreads out to the rest of the nodes on the network. This is called a “gossip network” since communications are passed from node to node until they are known by the whole of the network. As a result, messages may be repeatedly sent to peers who have already received them from other peers. The time it takes a message to find a path to all members of the network is random and can be non-trivial. Delays in communicating newly mined blocks, for example, is one of the reasons that Bitcoin experiences forks.8
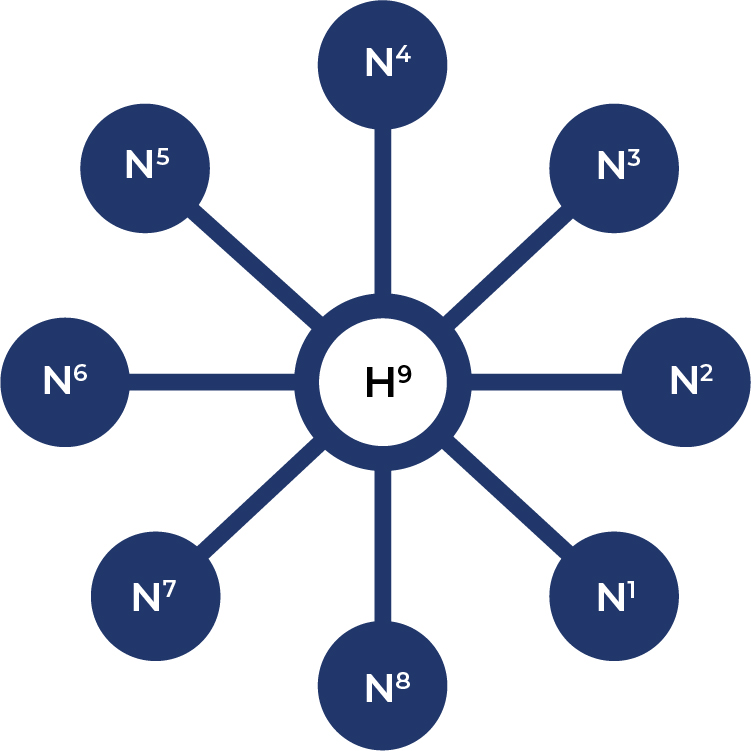
Geeq uses a hub and spoke instead of a gossip network structure. Hub and spoke is more efficient than a gossip network since it transmits the minimal set of messages possible and allows them to reach the entire network more quickly. Each node serves as a hub for one block and then passes the job to the next node in line. For example, a nine node network with node number nine serving as the hub would look like the following:
Summarizing:
- The Geeq ecosystem has no master-chain nor any central point of failure.
- Geeq is a permissionless, public blockchain platform validated by anonymous nodes that can join or leave any given validation network at will.
- Each instance of a geeqchain has its own independent set of validating nodes and maintains validation and application layers with separate blockchains.
- Any number of instances of geeqchain can be created and this allows the ecosystem as a whole to scale to handle as many Transactions Per Second (TPS) as needed.
- Geeq is a network of networks forming an ecosystem of interoperable blockchains.
- $GEEQs can be freely transferred across all chains in the ecosystem and applications can be designed to interoperate as needed.
- There is an elegant upgrade path that does not punish users. If users find a better alternative, they are free to vote with their feet.
4. Building and Validating Geeqchains
4.1 Geeq’s Workflow
Geeq also takes a very different approach to building a chain and keeping a ledger than existing protocols. This begins with Geeq’s workflow:
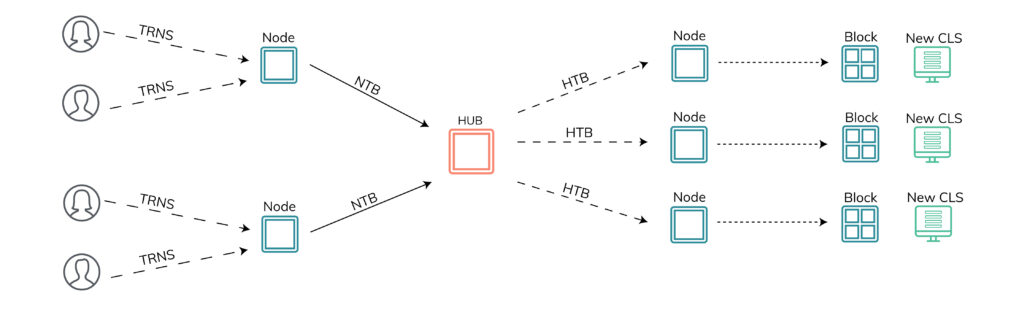
- A user chooses any node in the validation network of the chain he wishes to use and sends it a transaction request.
- Nodes wait for transactions to arrive (ten seconds by default) and then group these requests into a Node Transaction Bundle (NTB), generate a header, and cryptographically sign the whole thing with their private keys.
- Nodes send these NTBs to the current hub.
- The hub groups these NTBs together into a Hub Transaction Bundle (HTB), signs it with its private key, and then sends the HTB back to each of the nodes.
- Each node separately and independently considers each candidate transaction in the HTB and builds the next block in the chain with the ones that it deems to be valid.
- Each node updates its view of the Current Ledger State (CLS) using its block of valid transactions.
- In the meantime, new transactions requests from users have been arriving at the nodes. Once each node commits its block, it builds another NTB and sends it to the node acting as hub to coordinate the building of the next block.
There are three things to emphasize here:
- Each node gets exactly the same set of candidate transactions in the HTB to evaluate for each block.
- If each node starts out with the same CLS and considers the same set of candidate transactions, they should all reach identical conclusions about which transactions are valid, what the next block is, and how it updates the CLS to get to the next ledger state. If nodes reach different conclusions, then some nodes must be dishonest.
- The header of each NTB must include the hash9 of the node’s view of the CLS and the correct block it just constructed. We will see below why this is important.
4.2 The Geeq Consensus Protocol
Proof of Work consensus protocols choose a block proposer or leader through a cryptographic race to solve a check and guess puzzle. Nodes “mine” the block by expending enormous computational resources trying to find the solution (called a “nonce”). The first node to solve the puzzle transmits its block to other nodes over the gossip network. If a node (called a “miner”) receives a correct, and correctly mined, block, it is supposed to stop working on his own block, commit the block it just received to the chain, create a new candidate block of correct transactions, and start the process of mining all over. Only the successful miner receives transactions fees and mining rewards.
Proof of Stake consensus protocols use voting mechanisms to decide if a proposed block should be committed to the existing chain. Leader selection methods and voting rules vary, but the most common approach is to give nodes different voting weights in proportion to the fraction of the tokenbase they hold or have had delegated to them by other nodes.10 Thus, wealthier nodes have more influence on whether a block is committed. In almost all cases, two thirds of the stake weighted vote is required for a block to be approved.
Geeq takes a fundamentally different approach. First, the Geeq Protocol has no leaders or block proposers. The hub coordinates building the block by collecting and distributing the NTBs sent in by the nodes, but it does not choose a set of candidate transactions from a mempool or anywhere else. In addition, the hub does not judge the validity of the transactions in its HTB nor does it propose a block for the other nodes to commit. Second, nodes do not vote on HTBs or blocks in any way. Instead each node decides on its own which transactions in the HTB it thinks are valid, what the next block should be, and how this should update the ledger state.
Of course, for a blockchain to be of any use, there must be agreement on the state of the ledger and the set of valid transactions that led there. In other words, there must be a canonical ledger state that honestly reflects the canonical chain of valid blocks and transactions. Geeq achieves this using a multilayered security model.
The first security layer incentivizes nodes to police themselves using a game theoretic mechanism called the Catastrophic Dissent Mechanism (CDM). To get a sense of how this works, recall that nodes must place hashes of their new blocks and CLS in the NTBs they send to the hub in the next round. If all nodes are honest, all nodes will come to the same correct conclusions. The only way for a node to reach a different conclusion is to be dishonest and choose to deviate from protocol. Honest nodes would immediately see from the NTBs that certain nodes were dishonest since the block and CLS hashes were different from their own. The CDM allows honest nodes to write audits against dishonest nodes and collect their GBBs as a reward. This simple mechanism gives us two remarkable things:
- If even a single node is honest, it will write audits against dishonest nodes, collect their GBBs, and throw them out of the ANL on its version of the ledger. More importantly, an honest and correct version of the blockchain and CLS will exist (along with many other versions that may be incorrect and dishonest). Again, we will see why this matters below.
- Honest behavior (meaning that all nodes strictly follow protocol) is a “coalition-proof equilibrium”.11 Put another way, honest validation and following protocol gives nodes a higher payoff than any alternative strategy available to any coalition of validators including the grand coalition (all the nodes acting together). Even better, universal honesty is the only coalition-proof equilibrium. Thus, the CDM provides what we call Strategically Provable Security (SPS). This is much stronger than “Nash equilibrium” which is only proof against deviation (dishonesty, in this case) by single nodes acting alone.12
The second security layer makes users, rather than nodes, the ultimate arbiters of the correctness of transactions, the blockchains, and the ledger states. Well-designed blockchains are auditable in the sense that if an observer has access to the history of the chain going back to the genesis block, he can calculate the correct CLS himself. Thus, any observer with enough information can prove for himself whether the view of a chain and ledger being kept by a node is honest or dishonest. The problem is there is nothing a user can do if he discovers that a node is dishonest under existing protocols. If the majority of the hashing power or the majority of the stake decides to approve incorrect transactions and add them to committed blocks, the user can either accept the lie or walk away from his account.
Geeq uses an innovative protocol called Proof of Honesty (PoH). It works as follows: Users interact with geeqchains through a “user client”. This is a software application that makes it easy to use Geeq, but also allows users to protect themselves from dishonest behavior. When a user wishes to make a transaction, his client contacts a node and asks for the ANL. The user client then selects a node from the ANL at random and sends it a request for a proof that it is keeping an honest geeqchain.13 If the node is honest, it sends the proof, the user client verifies it, and the user sends the transaction. If the node can’t or refuses to prove its honesty, the client tries another node.
PoH seems simple, but the effects are profound:
- Suppose that at least one node is honest and is therefore writing an honest chain and ledger. Since any agent can tell whether a node is honest, why would any rational user ever accept tokens on a dishonest ledger if an honest one exists? Such tokens are likely to have been stolen, and are likely to be stolen from any user who accepts them. Thus, users who allow their clients to work in their interests will never be fooled into accepting payments on dishonest, and therefore, invalid ledgers. As a result, dishonest ledgers and the tokens they contain are valueless. Attempting to transact on a provably invalid ledger would be like trying to pass off a drawing of a $100 bill scribbled on a cocktail napkin as the real thing.
- PoH is 99% BFT.14 That is, if there is at least one of honest node, users will find it and only send and accept transactions on the ledger it keeps. Dishonest ledgers and nodes will be ignored. This is why it is possible for one or a small minority of honest nodes to enforce any audits they run against dishonest nodes and benefit from the confiscated GBB. Geeq’s protocol does not require votes from dishonest nodes to approve transactions or blocks.
- Each node is presented with the same set of transactions, keeps its blockchains and ledgers, and then users are provided with the tools to check the proofs for whether or not the node is behaving honestly.
Summarizing:
- Geeq has no leaders or block proposers.
- Each node decides for itself what the correct block and ledger is, and each user is able to prove to himself whether any given node’s view is correct. Thus, security come from the edge rather than from the center. Users rather than nodes are the ultimate arbitrators of truth.
- The CDM is an audit mechanism that implements honest behavior in coalition-proof equilibrium.
- PoH does not require that a majority of the hashing power or stake holders are honest. It only requires one honest node. Thus, PoH is 99% BFT instead of 50% or 33% like other protocols.15
There are several unanswered questions here. For example: What if all nodes are dishonest? What incentive do nodes have to spend the resources needed to create and send proofs of honesty, NTBs, and HTBs, as the protocol requires? How does Geeq prevent forks and deal with partitions? These problems are handled by additional security layers which are discussed in detail in our Technical Paper.
5. Why is Geeq a Better Solution?
Geeq offers unsurpassed security, unbounded transaction capacity, and extreme flexibility at a very low cost.
5.1 Security
Security Characteristics of Geeq and Other Protocols
Geeq’s PoH provides security in multiple dimensions compared to other protocols:16
- BFT: What fraction of dishonest nodes can a protocol tolerate and still work securely? BFT is the most common measure of security discussed for blockchain protocols: the higher, the more secure a protocol is considered to be.
- Edge Security: Does the protocol allow account holders to protect themselves from dishonest nodes or networks? In other words, do account holders have any immediate, independent actions they can take to avoid the theft of their tokens due to dishonesty on the part of validators? See the Technical Paper for a longer discussion.
- Equilibrium Type: If honest node behavior is an equilibrium of the protocol, what type of game-theoretic equilibria is it?
- Multiple Equilibrium: Are there any other stable equilibria besides honest behavior that should cause concern? For example, when there are multiple Nash equilibria, many may be undesirable. (See the Prisoner’s Dilemma for the most famous example.)
- Sybil-Proof: Is the protocol invulnerable to the creation of false identities with multiple nodes being controlled by one real-world agent?
- Wealth-Proof: Is the protocol invulnerable to attack by agents with lots of resources to buy tokens or computational power?
- Nation State-Proof: Is the protocol invulnerable to state actors?
- Anonymous: Are the nodes in the validating network anonymous?
- Trustless: Is the protocol free from the need for a trusted party or trust between parties?
5.2 Cost and Scale
Limitless Scalability at Very Low Costs
Transactions on Geeq cost very little. This is mainly because the validating networks are relatively small, the networks are efficient, message and record formats use minimal storage and bandwidth, the stakes needed for nodes to participate are modest, and no electricity or computational cycles are wasted doing Proof of Work.
Geeq is a low cost, highly secure, interoperable, multiple chain platform. Its architecture allows Geeq to scale without limit at a transaction cost of 1/100th of 1 cent.
Limitless scalability at low transaction costs enables Geeq to use its comparative advantage in blockchain security to create several new markets, discussed below in Section 6. The Geeq Platform was designed to take the following practical considerations into account.
Network Size: Using more nodes leads to higher costs and lower TPS.
- Bitcoin and Ethereum have many thousands of nodes in their networks all doing expensive proof of work.
- PoS has many variations. In some, stake is delegated by token holders to a smaller number of voting nodes. In this case, only a few nodes actually participate in validating transactions and communicating on the network. Others, such as Algorand, require all users to be ready to participate in the validation network.
- A single instance of a geeqchain can process 40-200 TPS depending on available bandwidth and network configuration.
- The maximum tps of the Geeq Platform, using current technology, is 200xN where N = the number of geeqchains on the platform at that moment.
TPS: transactions per second.
- Since any number of geeqchain instances can be created, the transaction processing capacity of the Geeq ecosystem is unbounded.
- PoW blockchains typically have large networks and heavy computational loads. As result, TPS is low, typically, 2-25 TPS
- PoS systems with small networks can achieve several hundred TPS and even more if they are run on cloud servers that give them unlimited bandwidth.17
- Every other protocol of which we are aware has either a single blockchain (or DAG), or a single master-chain. Although transactions may be submitted quickly, these structures inherently experience more difficulty as volume increases. In contrast, Geeq is a truly decentralized system of interoperable blockchains.
Transaction costs:
- The resources used by an instance of a geeqchain are very small and are roughly proportional to the size of the validating network the instance uses. Computational resource costs are between 1/1000¢ and 1/100¢.
- PoW blockchains must pay for the costs of the large amounts of electricity used to validate the ledger. In addition, such blockchains are slow and this creates a scarcity of transaction slots. In turn, this forces users to offer high fees in order to get their transactions included in the next block.
- There is such a variety of PoS approaches, it is hard to generalize about transaction fees. However, users ultimately must pay validators for the opportunity cost of locking up tokens to gain voting stake and for the costs incurred by the network. Together these can be substantial, and in any event, are larger than the costs of running an instance of geeqchain.
- Some public DAGs, such as Iota, claim to have zero transaction fees. However, the graph they create is a very large data item and users must be have knowledge of a significant part in order to know that a transaction is valid and finalized. Some DAGS also require a limited amount of PoW to discourage Sybiling. The upshot is that to be sustainable, these non-trivial costs must be covered by the system’s users either through transaction fees or contributions of resources to the network.18
- Private DAGs and PoA blockchains can be relatively inexpensive to run in terms of compute, bandwidth, and storage resources. Often, the validation networks that support them are relatively small. However, there can be significant setup costs, licensing fees, and ongoing support expenses for private solutions such as these.
5.3 Geeq’s Stabilized-Token
Drawing on economic lessons in the real world, Geeq has designed an Algorithmic Monetary Policy (AMP) to let platform use and token demand rather than speculation be the primary drivers of token value. Geeq’s tokenomics is centered on the idea of creating a middle path between the impracticality19 of a fixed exchange rate stable-coin, and the uncertainty and volatility of an unsupported, free-floating token. The result is a Stabilized-Token which limits the influence of speculators, dampens the impact of fear, uncertainty, and doubt, and creates a more predictable and stable environment to support and sustain adoption and usage for all Geeq platform participants.
Geeq’s AMP works by slowly expanding the tokenbase as $GEEQ’s price goes up to generate a fiat cash reserve that will be used to support $GEEQ’s price if it should ever start to decrease. More specifically, the AMP creates a predetermined, publicly known, additional supply of tokens in bull markets, and additional demand in bear markets by using the reserve to repurchase tokens and remove them from circulation. The size of the circulating tokenbase is therefore automatically adjusted to reflect the actual needs of the users of the platform. This does not prevent the $GEEQ’s value from increasing, nor does it guarantee that its value will never fall. What it does is fund a kind of insurance policy in good times that can be deployed to reduce the impact of bad times. The fact that there is a prefunded commitment to defend $GEEQ’s value can dampen or stop low-information expectations-driven price changes. See our Monetary Policy for more details.
6. How to use Geeq
Geeq has several features that set it apart from other platforms. Geeq aims to become a leading provider of solutions for key blockchain use cases.
6.1 Tokenization and Payments
$GEEQ is a purely transactional cryptocurrency. Its primary use is to pay the validation networks for their services and allow validators to stake GBBs. Geeq’s 99% BFT, SPS, stabilized-token AMP, and low transaction fees make it ideally suited for the following:
Payments – Approximately 6500 merchants accepted crypto-payments in 2018 including Microsoft, Newegg, Overstock.com, Namecheap.com, and Shopify.com.20 Geeq offers a much more secure ledger than any existing blockchain platform and has a monetary policy meant to reduce its volatility. Couple this with low transactions fees, and $GEEQ is positioned to become a very attractive general purpose cryptocurrency.
Escrows – Escrows are used to make sure both parties to a transaction perform as they promised. Money is commonly held in escrow for property sales and for delivery of goods that are on order. In supply chain applications, escrows can last three months or more. If token price is volatile, the value held in escrow can end up being significantly less than expected when it is eventually released. Both parties must build in this risk when constructing smart contracts. Geeq’s stabilized-token AMP is constructed to make it safer for such uses than free floating cryptocurrencies such as Bitcoin and Ethereum.
Remittances – $GEEQ’s relative stability also is likely to make it a good choice for remittances sent to countries with unsound monetary polices that generate inflation as well as for a more general store of value.
Tokenization – The idea of moving securities trading to blockchain platforms has been widely discussed. This is done through “tokenizing” shares of stock by creating a special token that legally represents ownership of share. It is then easy to keep track of portfolios in a blockchain ledger in a way that preserves privacy, lowers transactions costs, and speeds settlement time. The problem is that existing platforms are simply not secure enough. If trillions of dollars worth of equities were traded on Ethereum, for example, many hostile actors (think China, North Korea, and even privately controlled bot-nets) would find it worthwhile to launch a 51% attack if only for the economic chaos it would cause.21 Geeq’s strong security model makes it realistic at last to consider tokenizing financial markets, land title registries, and other high value items.
6.2 High Volume, Low Value Transaction Applications
Existing blockchain platforms have relatively high costs and limited scalability. Geeq, on the other hand, is infinitely scalable due to its multi-chain architecture, has low transactions costs, and is customizable as a result of its separate application layer. This gives Geeq an enormous comparative advantage in use cases with high volumes of low value transactions. This may not sound very glamorous, but it opens to door to some truly transformative applications.
Internet of Things (IoT): Billions of connected, smart devices are produced every year. The Internet of Things includes consumer items such as TVs, thermostats, security systems, washing machines and cars, industrial equipment such as pipeline sensors, electrical grid switches, drones, devices used in hospitals, agriculture, education, and smart cites, etc. All of these devices produce huge volumes of telemetry. Although each individual piece of telemetry might not have much value, certain pieces, or the telemetry stream as a whole, can be very valuable indeed. Consider the following:
Compliance and Liability – Recording real time, contemporaneous records, and then keeping them in a tamper-proof and secure way, allows companies and others to inexpensively prove that they are in compliance with various regulations or that they followed correct procedures. Examples include medical monitors and devices, infrastructure devices such as transformers, substations, water mains, gas pipelines, communications grids, roads and bridges, and industrial and agricultural devices.
Transparency and Accountability – As the technological ability to collect and analyze data grows, it is ever more vital that governments and corporations be as transparent as possible. Examples include police dash and body cameras, environmental readings, and electronically created public and accounting records. If nothing goes wrong, then it is unlikely that anyone will have any interest in such data. However, when an incident happens, geeqchains are able to provide trustworthy records that show exactly what transpired, where responsibility lies, or proof that parties behaved correctly. Knowledge that such records exist creates incentives for corporations and government agencies to make sure they are behaving properly and increases public confidence in such institutions.
Machine to Machine Markets – Blockchain opens up the possibility of allowing devices to work as agents in their owners’ interests. When you are traveling in a foreign country, for example, your cell phone could use an app to wirelessly reach out to and negotiate with other cell phones for bandwidth on the local network. Payments would be securely made in $GEEQ without the need for either device owner to get directly involved. Buyers would get connectivity despite being out of network, and sellers would make a profit. Other examples include allowing computers to sell unused compute cycles or excess storage to other computers with a shortage, and matching cars to parking places or to slots on the highway during the morning commute.
The common thread running through these use cases are that they require that a huge volume of telemetry or other transaction types to be certified and made available when needed. This is only possible on a blockchain that can scale at low cost. Instances of geeqchain can easily handle 200 TPS or more at a cost of $.0001 (a hundredth of a cent) or less. The table below gives some example of the number of transactions and annual cost for devices writing telemetry hashes on Geeq at various rates.
High Volume, Low Cost IoT on Geeqchains
Micropayments – At present, there is really no good way to make micropayments.22Credit cards have high fixed transaction fees, and making small ACH payments from your bank account is difficult and risks exposing private financial information. One of the great promises of blockchain technology is that it would provide a solution. Unfortunately most popular cryptocurrencies have high transactions costs, long finality windows, and are cumbersome to use. If micropayments were feasible, it would open many disruptive possibilities:
- Peer to Peer Content Platforms: Individual content producers such as musicians, writers, photographers, visual artists, and video creators are forced to use platforms such as YouTube, SoundCloud, Shutterstock, and Etsy to distribute their work. These platforms impose their own rates of payment, promote content as they choose, and can also remove or censor content they don’t like. Geeq micropayments allow creators and consumers to connect directly without a platform imposing rules or taking a cut. This makes it possible for talented creators to make a living and gives consumers access to a much wider array of offerings.
- Streaming Payments: Access to streaming services are also intermediated through various platforms. Transactions costs make it impractical to use pay-as-you go approaches and so platforms typically use a monthly subscription model. Geeq micropayments make it feasible to charge (or pay) users a few cents at a time. Gaming by the minute and renting or buying useful items within a game become possible, as do streaming payments for live services such as tech support, medical, professional or even mechanical Turk-type services.
Note that the transaction volume that these use cases would require is enormous. It certainly exceeds the scale of any existing blockchain platform, and even has the potential to overwhelm the scale of the Visa/Mastercard network. The reason we do not see such applications now is that existing blockchain platforms are too limited and too expensive to make them feasible. Geeq changes all this. Not only is Geeq inexpensive and scalable, but it is designed to support instances that are specialized and optimized for use cases that make it possible for the data from an individual device or streaming payments from a single video to be recorded under pre-determined, mutually agreeable terms that a powerful market player cannot change unilaterally.
6.3 Distributed Business Processes
Distributed business processes are an ideal application for public blockchain. Use cases include logistics chains, proving provenance, and real estate transactions, among many others. These have been well-explored, and numerous projects exist that focus on specific verticals. Many of these processes require escrows, payments (micro and macro), the recording of large amounts of sensor telemetry, chain of custody receipts, signed documentation, and/or need audit trails. We have already discussed Geeq’s comparative advantage in these areas. We focus here on why the architectural features of the Geeq platform make it a better foundation on which to build these sorts of application.
Security is of vital importance for chains devoted to:
- Chain of custody for controlled or dangerous substances
- Digital asset records
- Infrastructure control
Interoperability, upgradability, and the flexible customization that Geeq’s application layer allows are critical for chains devoted to:
- Medical and financial records that need to remain private even after quantum computing becomes practical
- Real estate, title transfers, and certain types of public records where chain data needs to be available for decades in an immutable and accessible form
- Distributed business processes that need complicated permissioning structures to maintain privacy, comply with regulations, or restrict access to proprietary data to authorized parties. Examples include medical, educational, and employment records
Adherence to the principle that “code is law” is important for blockchains devoted to:
- Free speech
- Property ownership
- Payment networks
7. Business Model
The fundamental purpose of blockchain is to align incentives so that agents can interact and work together without needing to trust one another. Geeq’s business model is structured with this as its core principle.
7.1 Transaction Costs
Nodes must be compensated for the services that they provide to the network. No platform can provide services for free and be sustainable. Costs could be covered by direct fee payments from users, indirectly through advertising or data collections (as Libra plans to do) or through in-kind contributions of computational services (Algorand, for example, seems to requires all users to participate in the validation network).
One might think that paying nodes with newly mined tokens, like Bitcoin or Ethereum do, compensates nodes without the need for direct transactions fees being charged to users. There are at least two problems with this. Most obviously, mining is inflationary. All else equal, creating new tokens is like taxing users on their holdings. Even if token value goes up, it would have gone up more in the absence of mining. Of greater concern is that it ties the security of the chain directly to token value. Bitcoin is trading at about $10,000 as of this writing which is half of its peak value. This means that current mining rewards are worth half as much, and therefore equilibrium mining effort will also be half what it was at its peak. It might be acceptable for a chain with half the tokencap to be half as secure, but if the chain also carries tokenized equities, land titles, valuable personal information, or important smart contracts, this become a matter of serious concern.
Geeq’s basic business model is to charge users a fee equal to approximately three times the cost of the computational resources needed to process transactions. Two thirds of this is used to pay nodes for their services and the remaining third is paid to Geeq. This gives both nodes and Geeq a net profit equal to the costs of running the network. Since the network uses very few resources, transactions fees are on the order of 1/100¢. Note, however, that while the efficiency of the network keeps Geeq’s validation costs low, DApp developers are free to set their own fees for the use of applications they build on Geeq.
To get a better sense of what the business model means in practice, consider a single instance of a geeqchain running at only 20 TPS23 with a 25 node validation network. This might be a telemetry chain supporting 1200 devices doing minutely writes, for example. Such a network would generate approximately 630GB of data per year to be stored in 3.1M blocks containing 200 transactions each. Transactions have a resource cost of around $.00003 each. Users would therefore be charged $.0001, or one one hundredth of a cent per transaction.
Summarizing:
- A 25 node network running at 20 TPS allows 630M transactions per year and creates 630GB of chain data.
- Transactions cost users $.0001 each and this generates a total of $62k revenue per year.
- Approximately $1.7k in $GEEQ is paid to each node per year for their validation services.
- Geeq receives $21k in annual revenue from one such geeqchain instance.
7.2 Services
The revenue sharing model described above creates an incentive for Geeq to grow the platform as rapidly as possible. To further this end, 10% of new token revenue from the AMP will be set aside to support Geeq developers and foster the community. This will fund hackathons, provide grants for creating code libraries that can be used by DApp developers, sponsor events and learning opportunities for coders and others interested in Geeq, and do other forms of community outreach across the world and with partners.
Geeq is a highly flexible and more secure platform than any currently available. The larger the community building applications and experimenting with Geeq’s technology, the more quickly its benefits will become apparent. Geeq certainly does not have a monopoly on creativity, insight into the best way to solve problems, or even on which use cases could most fruitfully be addressed by blockchain as a service. We believe specialization, comparative advantage, and diverse approaches create benefits for all. It only makes sense for Geeq to have an inclusive philosophy.
Geeq will also jump-start this process by writing its own turn-key applications that can be customized for use by enterprises, businesses, and other organizations. Our focus will be on developing high volume, low value transaction applications that are Geeq’s comparative advantage. Financial transactions, micropayments and telemetry are obvious examples. More generally, Geeq will provide development services to help customers create applications that utilize Geeq’s unique feature set. Unlike many projects in which founders benefit primarily or exclusively from money raised through token sales, Geeq’s team profits mainly if it continues to build, expand, and improve the platform. We do not ask users or developers to trust us to look after their interests, this is blockchain, after all. Instead we ask users to verify that if we do what is best for us, we must be doing what is best for them as well.
7.3 A Tokenomics Example
The value of any currency, crypto or fiat, is determined by the Quantity Theory of Money (QTM).24 Calling this a “theory” is misleading. The QTM is actually an accounting identity which is true by definition. As a result, the QTM is the engine that drives the value of cryptocurrencies at the most basic level. Formally, the QTM can be expressed in the following equation:
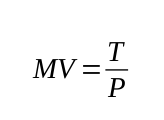
where:
T = Transactions volume (the value that is transacted using a currency)
V = Velocity of money (the number of times a dollar bill or token is transacted per year)
M = Money supply (the total number of dollar bills or cryptotokens in existence)
P = Price (value of a token or unit of currency relative to commodities or other currencies)
Geeq will create 100M tokens with a nominal issue value of $.25 giving an initial tokencap of $25M. Suppose there were 1000 instances of telemetry chains as described in section 6.1 in existence and each node had 1500 $GEEQs (worth $375 or about 20% a node’s annual revenue) staked as a GBB. This would mean that 37,500 $GEEQs were locked up on each chain. In total this implies 37.5M of the 100M $GEEQ coinbase would not be circulating (and therefore have zero velocity). Since annual transactions fees total $62k per chain, 1000 chains would generate $62M in revenue (and therefore, transactions volume). Suppose that circulating $GEEQs changed hands four times per year (implying a daily velocity of about 1%). Then applying the QTM: P = $62M/(62.5M× 4), we conclude $.25 would be the equilibrium value of $GEEQ.
If 2000 instances existed, 25M $GEEQs would remain in active circulation and $124M in total fee transactions would take place. We can apply the QTM to find the velocity that would allow $GEEQ to remain at $.25 as follows: V = $124M/($.25 × 25M), which means that each $GEEQ would need to change hands 20 times per year implying a daily velocity of about 5.5%. This is consistent with what we actually see for Bitcoin and other cryptocurrencies. If velocity were lower than this, however, the token price would have to rise.
In terms of profit, Geeq would make $21M or $42M in each of these scenarios, respectively. The network of validators would get paid $42M, or $84M, respectively, of which we estimate half is profit.
Note that all transactions demand in the examples above comes from transactions fees alone (at one one hundredth of a cent each). If $GEEQs were also used for micropayments or as a general transactional currency, transaction demand could be considerably higher. Bitcoin has daily transaction volumes ranging from $4B to $20B. About half of the top 50 cryptocurrencies had daily volumes of $50M25 or greater. which imply more than $180B in annual transactions demand each (compared to our example which assumed only $124M, or less than 1/1000th, of this volume.) Going further down the list, about half of the tokens ranked between 150 and 200 by tokencap had daily volumes over $1M which would imply $365M or more in annual transactions value.
Putting this together, the more $GEEQ (or any token) is locked up as stake for voting, bonds for good behavior, in smart contracts, or as a store of value, the higher the token’s value, all else equal. Similarly, the more transactions demand, the higher a token’s value. Conversely, higher velocity implies lower token value, all else equal.
8. Conclusion
Geeq is a scalable, inexpensive, and computationally light approach to creating an ecosystem of flexible, interoperable and extremely secure blockchains. Geeq’s Proof of Honesty consensus protocol gives geeqchains 99% Byzantine Fault Tolerance, Strategically Provable Security, and makes users, rather than nodes, the ultimate judges of truth.
We envision an ecosystem with thousands of interoperable instances of geeqchain doing a wide variety of tasks that are currently not possible. Geeqchains can be built to run standard payment networks, support distributed business processes, construct various kinds of two-sided markets, and all the other applications typically discussed in the context of blockchain platforms.
Geeq’s security model makes it invulnerable to hostile actors who may have access to resources that could overwhelm blockchains based on PoW, PoS, PoA, or DAGs. This makes it possible for the first time to consider moving exchanges, banking, high value information and records, and critical applications, out of private databases and onto blockchain.
What makes Geeq truly unique is that DApps built on the Geeq Platform will be able to securely process massive volumes of transactions on specialized instances at a cost of 1/100th of a cent or less. This is not simply an incremental step, it is transformative.
Costs this low make it feasible to record telemetry from the billions of IoT devices that are increasingly in control of our electronic and physical environments. The existence of records that are held on a provably tamper-proof ledger creates accountability, decreases potential liability, increases transparency, and protects privacy. Low cost streaming micropayments allow content creators and service providers of all kinds to sell directly to consumers instead of depending on centralized platforms. Micropayments also enable machine to machine markets and allow devices to act in the interests of their owners instead of their manufactures.
Geeq’s business model makes each instance independently sustainable without the need to interact with any mother-chain, or the possibility of interference from Geeq or any other authority. Once an instance of a geeqchain is created and released into the wild, it has a life of its own. More generally, the availability of a low cost way to store information in an immutable, uncensorable, and distributed way provides a mechanism for people to establish sources of provable truth that are independent of governments or other centers of power and authority.
Photo by Christian L on Unsplash
Notes
- GeeqTM, geeqchainTM, GeeqosystemTM, Proof of HonestyTM, PoHTM, Strategically Provable SecurityTM, SPSTM, Catastrophic Dissent MechanismTM, CDMTM, Stabilized-coinTM, and Stabilized-tokenTM are all trademarks of Geeq Corporation.
- BFT comes from Lamport, Shostak, and Pease (1982) in which they describe “The Byzantine Generals Problem”. To understand the idea, suppose that ten generals of the Byzantine empire are surrounding a city, some of whom have been bribed not to attack. Suppose the participation of at least seven is required in order to conquer the city. Otherwise, the attack fails. Such a battle plan is said to be 30% BFT. Most blockchain protocols have BFT of 50% or less. More generally, BFT is a measure of how tolerant a system is to faulty components. Unfortunately, characterizing robustness in this way tends to make protocol designers think of nodes as parts of a system that either work as expected, or fail, instead of as rational agents with preferences who are capable of doing either depending upon the circumstances. Geeq’s security model is based on game theory and economic mechanism design. Honest validation by all nodes is the only coalition-proof equilibrium of Geeq’s protocol. This provides Strategically Provable Security which is an even stronger security guarantee than 100% BFT. See the companion Technical Paper for more details and a proof of this claim.
- It is difficult, however, to see a reason to use a private, permissioned blockchain such as IBM’s Fabric or permissioned DAGs such as Hashgraph. Doing so simply introduces the overhead of a consensus layer and requires reducing the complexity and utility of the data so it will fit into a blockchain ledger structure without getting rid of the need for mutual trust between all parties. Using a shared database makes far more sense.
- Telemetry is a term for the stream of data that connected machines send back to their owners or manufacturers. This includes everything from temperature, vibration, and flow measurements, to clickstreams, video recorded by surveillance cameras, and conversations overheard by smart speakers.
- Note that at best, governance is 50% BFT. A great deal of economic research in voting theory and public choice proves that it is essentially impossible to create non-manipulable mechanisms that are in any way fair, equitable, or efficient. The most famous are the Arrow Impossibility Theorem (Arrow 1950) and the Gibbard-Satterthwaite Theorem (Gibbard 1973 and Satterthwaite 1975). Section 3.2 discusses how Geeq is able to upgrade and change over time without having trusted agents or committees, governance rules, or breaking faith with users.
- Hard forks are usually imposed by nodes who collectively decide to alter basic protocol elements or roll back the ledger to invalidate transactions that they consider to be illegitimate. Often this is coordinated by foundations or leaders associated with a given blockchain project. In other cases, the network splits with some nodes choosing one ledger state and/or protocol and the rest choosing another. This can be confusing to users who may have accounts on both forks or who may be asked to choose which fork should hold their accounts. Many new projects include governance systems which make it even easier to change protocols and invalidate “finalized” transactions through voting, staking, or other mechanisms. Individual users at large do not have any control over what form a blockchain with governance might take in the future. In contrast, Geeq empowers each and every individual user to either accept or reject any proposed change to protocols. Even if all the current nodes and/or a majority of users decide to move to a new instance based on a new genesis block, any users who wish to stay with the original protocols and ledger state may do so. New nodes will appear and offer their validation services to those who stay since they are compensated at the same rate as nodes on the new instance.
- Of course, it would also be possible to create a new token native to the application layer that would function as ETH does. Payments to nodes, however, would still be made in $GEEQ and recorded on the validation layer blockchain.
- A “fork” occurs if different blocks are added to the same root chain by different sets of nodes. This results in two (or more) incompatible views of the ledger being held by different parts of the network. Both versions of the chain and ledger may be correctly maintained, even though they contain different sets of transactions. Eventually, one of these forked chains becomes longer than the other and is then considered to be canonical (the only valid chain). The problem is that users who accept bitcoins on one of these forks may find that their transactions are erased if their fork ends up being orphaned as the shorter chain. Bitcoin users have no way of telling which fork will eventually become canonical and which will be orphaned and so may lose their bitcoins even though they acted in good faith, followed protocol, and made sure they were sending their transactions to honest nodes maintaining a correct chain.
- Hashes are sometimes referred to as the “fingerprint” of a digital file. Running any file, regardless of length, through a hash function (such as SHA-256) returns a (256 bit) binary string. Running the same file through the hash function always gives the same string. Running any other file through the hash function, no matter how similar, returns a different string. Thus, if all NTBs have the same block and CLS hashes, then they all share the same view of what they contain. Otherwise, different nodes have different views. See Conley (2019b) for a simple explanation of encryption and hashing technology.
- See Larimer (2014) for more discussion.
- See Bernheim, Peleg, and Whinston (1987) and the discussion in Conley and Konishi (2002) for a more formal description of coalition-proof equilibrium.
- Nash equilibrium and even dominant strategy equilibrium are far too weak to be of value in the context of blockchain where Sybils, mining pools, and coalitions of bad actors are the norm. This aside, all PoW and PoS protocols of which we are aware have many, usually an infinity, of Nash equilibria. There is absolutely no reason to believe equilibria where desirable behavior, such as having a sufficient number of validators behaving honestly, is more likely to be seen than one of the many other bad equilibria that could occur. See Eyal and Sirer (2014) for one of many examples of Nash equilibria for blockchains that destroy their security.
- Structuring the data in Geeq ledgers and chains and building in ecosystem elements that make it possible for a node to prove it is keeping a honest ledger while requiring relatively small amounts of data to be transmitted is central to Geeq’s architecture.
- Although we call this 99% BFT, it is really (N-1)/N BFT where N is the number of nodes in a validating network. Thus, depending on N, PoH could have a larger or smaller BFT than 99%. If there are only ten nodes for example, PoH is 90% BFT, which is still much greater than the 50% or 33% seen in other protocols.
- In fact, PoS and PoW may be considerably less secure than even this. See Eyal and Sirer (2014) and Houy (2014) for a discussion of even lower cost and more direct attacks of these protocols.
- Distributed Acyclic Graph (DAG) approaches are not actually based on blockchain, but instead rely on repeated validation, hashing, and transmission of transactions by individual nodes. Eventually, users are supposed to gain confidence that a transaction is valid and finalized based on an evaluation of the number of and depth of independent confirmations and the reputation of the nodes involved. We won’t explore DAGs in detail here, but in general, the number of validators used is relatively small, validator anonymity is difficult to guarantee, and the protocols appear to be open to strategic manipulation on a number of fronts. For example, see Christine Masters’ discussion of Iota at: https://cryptovest.com/education/not-a-iota-the-trouble-with-iota-and-how-to-fix-it/, and Lansana’s discussion of HashGraph’s centralization and governance problems at: https://medium.com/@Lansana/i-was-wrong-hashgraph-is-actually-very-bad-bf7d9b2e8d99.
- Truly scalable solutions require sharding or some other approach to maintaining multiple, but still interoperable ledgers. The challenge is to do this without opening new attack surfaces or vulnerabilities through bridge chains, less secure side chains, or lightning networks. Even then the security guarantees cannot be greater than underlying consensus protocol, usually 33% or 50% BFT.
- See Elsts (2018) and Elsts et al. (2018) for a discussion of how such contributions make it difficult or impossible for IoT devices to participate in the Iota Network.
- See “ETFs Rule, Stablecoins Drool: How to Make Cryptocurrencies go Mainstream” for a more detailed discussion about the impracticality of stablecoins.
- https://www.virtualcoinsquad.com/
- Bonneau (2018) estimates that it would cost less than $1M per hour to rent enough capacity on EC2 to mount a 51% attack on Ethereum, and only $1.5B to outright purchase enough capacity to mount such an attack on Bitcoin. Given that Bitcoin’s token cap is approximately $140B at this writing, $1.5B seems like a relative bargain to gain full control. Other authors have placed the cost of a rental attack on smaller PoW blockchains such as EthereumClassic, Monero, and Dash at less than $10k per hour (see https://www.crypto51.app/). A number of such attacks have actually occurred on such chains.
- Markets exist to take advantage of gains from trade. When one person values something more than another person, they can agree on a sales price that leaves them both better off. But what happens when the gains from trade are on the scale of fractions of pennies? Markets in this case are only possible if transactions costs are less than the potential gain. It makes no sense to pay five cents to complete a transaction that is only worth half a cent.
- This is about 10% or less than the network’s full potential, so nodes would not be pushing the limits of available computational resources. The idea is to allow Geeq nodes to run as background processes on home computers.
- See Zero or Moon: What’s Up with the Price of Ethereum? for a simple explanation of the QTM in the context of Blockchain.
- As of August 27, 2019. See https://coinmarketcap.com/ for more current information.
References
Arrow, K. (1950). “A Difficulty in the Concept of Social Welfare”,Journal of Political Economy328–346, doi:10.1086/256963.
Bernheim, D., Peleg, B., and Whinston M. (1987) “Coalition-proof Nash Equilibria. I. Concepts”, Journal of Economic Theory, Vol. 42 pp. 1-12. doi: 10.1016/0022-0531(87)90099-8.
Bonneau, Joseph (2018) “Hostile Blockchain Takeovers (Short Paper)”, Financial Cryptography Workshops 2018, doi:10.1007/978-3-662-58820-8_7.
Castro, M. and Liskov, B (2002) “Practical byzantine fault tolerance and proactive recovery”, ACM Trans. Comput. Syst., Vol 20, pp. 398–461.
Conley, J. (2018) “Proof of Honesty: Coalition-Proof Blockchain Validation without Proof of Work or Stake” Manuscript, https://jpconley.files.wordpress.com/2019/08/proof-of-honesty-and-the-catastrophic-dissent-mechanism-for-secure-blockchain-validation-v-2.0-2019-05-31.pdf.
Conley, J. (2019b) “Encryption, Hashing, PPK, and Blockchain: A Simple Introduction”, Vanderbilt University Department of Economics Working Papers, VUECON-19-00013, https://jpconley.files.wordpress.com/2019/08/vuecon-19-00013.pdf.
Conley, J. (2018a) “Zero or Moon: What’s Up with the Price of Ethereum?” https://blog.goodaudience.com/zero-or-moon-whats-up-with-the-price-of-ethereum-ef6331007308.
Conley, J. (2018b) “ETFs Rule, Stablecoins Drool: How to Make Cryptocurrencies go Mainstream” https://medium.com/@JPConley/etfs-rule-stablecoins-drool-how-to-make-cryptocurrencies-go-mainstream-b713a054b311.
Conley, J., and Konishi, H (2002) “Migration-Proof Tiebout Equilibrium: Existence and Asymptotic Efficiency”, Journal of Public Economics, Vol. 86, pp. 243–62.
Crypto51.app (2019) “PoW 51% Attack Cost” https://www.crypto51.app/.
Elsts, Attis (2018a) “Lessons learned from evaluating IOTA on Internet of Things devices” https://hackernoon.com/lessons-learned-from-evaluating-iota-on-internet-of-things-devices-a44575e606de.
Elsts, A, Mitskas, E. and Oikonomou, G. (2018b), “Distributed Ledger Technology and the Internet of Things: A Feasibility Study” In Proceedings of the 1st Workshop on Blockchain-enabled Networked Sensor Systems (BlockSys’18), Gowri Sankar Ramachandran and Bhaskar Krishnamachari (Eds.). ACM, New York, NY, USA, 7-12. DOI: https://doi.org/10.1145/3282278.3282280.
Eyal, I and E. G. Sirer (2014) “Majority is not enough: Bitcoin mining is vulnerable” In Financial Cryptography and Data Security 18th International Conference, FC 2014, pages 436–454.
Geeq (2019) “Algorithmic Monetary Policy for the Geeq Stabilized-Token” White Paper, http://www.geeq.io/algorithmic-monetary-policy-for-a-stabilized-token/.
Gibbard, A. (1973) “Manipulation of voting schemes: a general result”. Econometrica Vol. 41, pp. 587–60.
Houy, N (2014) “It will cost you nothing to “kill” a proof-of-stake crypto-currency” Economics Bulletin, Vol. 34, pp. 1038-1044.
Lamport, L., Shostak, R., and Pease, M. (1982) “The Byzantine Generals Problem”. ACM Transactions on Programming Languages and Systems, Vol. 4, pp. 387–389.
Larimer, D. (2014) “Delegated Proof-of-Stake (DPOS)”, Technical Report, http://v3.bitshares.org/security/delegated-proof-of-stake.php.
Lansana (2017) “Why Hashgraph will never replace Blockchain” https://medium.com/@Lansana/i-was-wrong-hashgraph-is-actually-very-bad-bf7d9b2e8d99.
Masters, C (2017) “Not a IOTA: The Trouble With IOTA and How to Fix It” https://cryptovest.com/education/not-a-iota-the-trouble-with-iota-and-how-to-fix-it/.
Satterthwaite, M. (1975) “Strategy-proofness and Arrow’s conditions: existence and correspondence theorems for voting procedures and social welfare functions”, Journal of Economic Theory, Vol. 10, pp. 187–217.
VirtualCoinSquad (2018) “Businesses that Accept Bitcoin, Litecoin, Dogecoins and other Altcoins in 2018” https://www.virtualcoinsquad.com/.






To learn more about Geeq, follow us and join the conversation.
@GeeqOfficial